Cybersecurity Courses
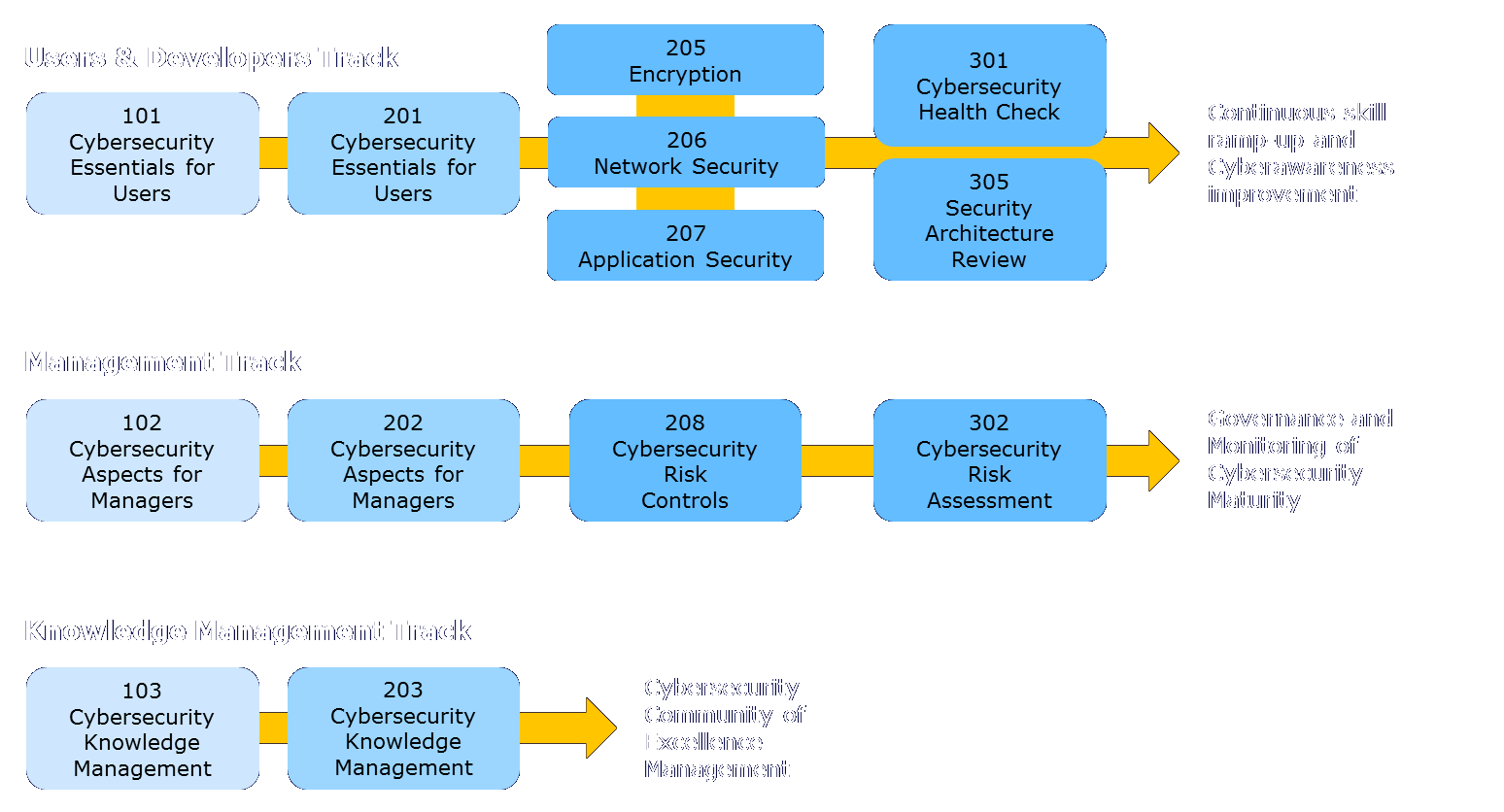
Cybersecurity Introduction/Skill Ramp-Up
The duration of some courses is given as a minimum to maximum number of days. The actual duration can be adjusted to accomodate desired depth of coverage, specific topics addressed, and the technological and organisational complexity of a customer environment to be considered.
- What is Cybersecurity?
- Cyberrisks and Mitigation Strategies
- Strategy, Technology, Governance
- Enabling a Cyberaware Organisation
- What is Cybersecurity for Management?
- Cyberrisk Categories and Management Controls
- Strategy, Technology, Governance
- Motivating a Cybervigilant Organisation
- Effective Knowledge Management Instruments
- Essential skills for a Cybervigilant Organisation
- Collaborative Learning for Threat Intelligence
- Facilitating a Best Practice Exchange in an Organisation
- Cybersecurity Drills and Assessments
Cybersecurity Advanced Topics
The duration of some courses is given as a minimum to maximum number of days. The actual duration can be adjusted to accomodate desired depth of coverage, specific topics addressed, and the technological and organisational complexity of a customer environment to be considered.
- Continuation of 101 – Practical Workshop
- 200 Cyberrisks and Practical Mitigation Strategies
- Strategy, Technology, Governance Applied
- Setting up a Cyberaware Organisation
- Continuation of 102 – Practical Workshop
- Cyberrisk Categories and Management Controls
- Strategy, Technology, Governance
- Motivating a Cybervigilant Organisation
- Collaborative Learning for Threat Intelligence
- Incentives and Motivation for Cybersecurity
- 200 Risks – Structuring the domain of Cybersecurity Challenges
- Knowledge Management Platforms for Cybersecurity
- Why encrypt information?
- Different types of encryption
- Effectively managing encryption in an organization
- Encryption tools integrating into work environments
- Hands-on workshop
- What is network security?
- Perimeter protection
- Protecting resources inside your network
- Under attack! Examples of hacking
- A secure network architecture
- IoT security issues
- Threat Intelligence
- What is application security?
- Best practices for application development
- Testing for Cybersecurity aspects
- Information classification - know what is valuable
- Multi-tier architectures: their complexity and their benefits
- Protecting data repositories
- How to measure Cybersecurity risk
- Cybersecurity risk controls
- Workshop: define and evaluate controls
- Information classification - know what is valuable
- Adequate reporting guidelines
Cybersecurity Reviews and Audits
The duration of some courses is given as a minimum to maximum number of days. The actual duration can be adjusted to accomodate desired depth of coverage, specific topics addressed, and the technological and organisational complexity of a customer environment to be considered.
- Identification of key business requirements and objectives for resilience
- Definition of key business risks (usually taking results from course 302)
- Assessment of security requirement fulfilment levels
- Rating
- Recommendations
- Identification of key business requirements and objectives for risk management
- Lessons from materialized risks of the past
- Assessment of impact and likelihood of individual risks
- Rating
- Recommendations
- Quick overall assessment of relevant aspects
- Information classification for applications
- Security architecture of multi-tier applications
- Cybersecurity aspects in application development
- Cybersecurity aspects in application testing
- Information classification for infrastructure zones
- Security architecture of multi-tenant IT infrastructure
- Cybersecurity aspects in infrastructure operations
- Maturity of the IT infrastructure and operations procedures
- Maturity of change management
- Recommendations
